# Configure AWS Cloudwatch for Log Forwarders
Jul 1, 2016 2 minute readAWS CloudWatch is a monitoring service to collect logs. It can be configured to accept multiple log sources. As with other AWS services Cloudwatch has detailed security and access control support. These are the steps I take to configure any log forwarder to Cloudwatch.
This guide will produce an Access Key Id and a Secret Access Key.
Configure an Access Policy
Policies are the backbone of AWS security. It is a good practice to write them as restrictive as possible. 1
1- Open the IAM Policies section
2- Select Create Policy 
3- Select Create Your Own Policy
4- Name it CloudWatchLogSender
5- Add the following text to the Policy Document section
{
"Version": "2016-07-02",
"Statement": [
{
"Effect": "Allow",
"Action": [
"logs:CreateLogGroup",
"logs:CreateLogStream",
"logs:DescribeLogGroups",
"logs:DescribeLogStreams",
"logs:PutLogEvents"
],
"Resource": [
"*"
]
}
]
}
What is this?: A policy that only Allows the actions CreateLogGroup, CreateLogStream, DescribeLogGroups, DescribeLogStreams, and PutLogEvents on any resource.
Create an AWS User
Having a specialized user just to forward logs can significantly limit the impact of any attack on the account. 2
1- Open the User Management Module
2- Create a new user named CloudWatchLogSender.
Make sure to save these security credentials because this is the last time you’ll see them
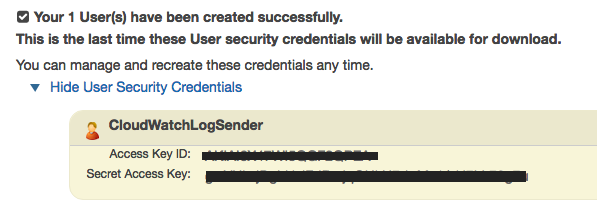
3- Open the CloudWatchLogSender user details page
4- Click the Attach Policy button in the Permissions tab
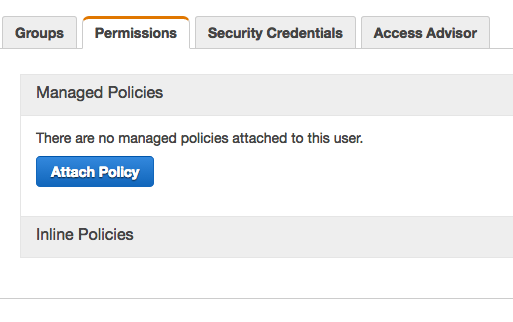
5- Attach the CloudWatchLogSender policy
Your user summary should look like this
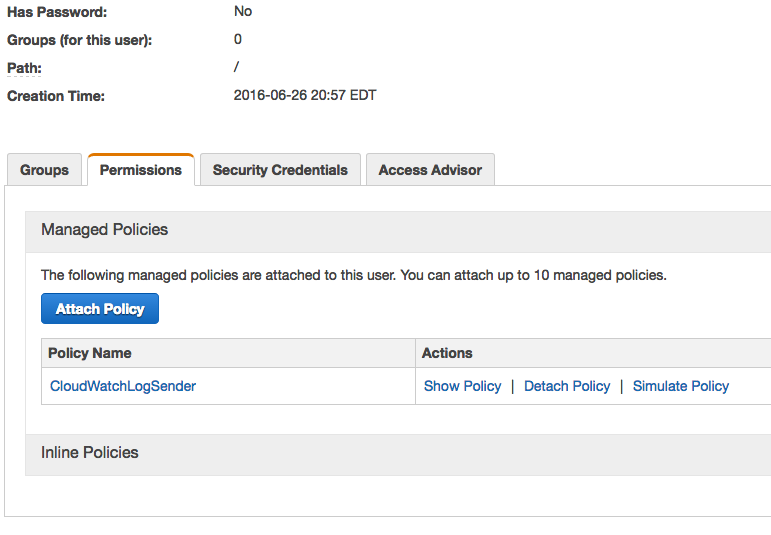
Summary
We have created the necessary security provisions to forward logs to AWS Cloudwatch from any source. Moreover, we have credentials that can be used by any forwarder compatible with Cloudwatch.
-
Restrictive access controls limit the risk of somebody using your account to mine Bitcoins or some other crazy thing. ↩